How it Works
How EDI/PDF order Automation works
Your Partner in Turning EDI/PDF order into clean,
ERP-ready data-fast accurate & fully auditable.
Smart Ingestion
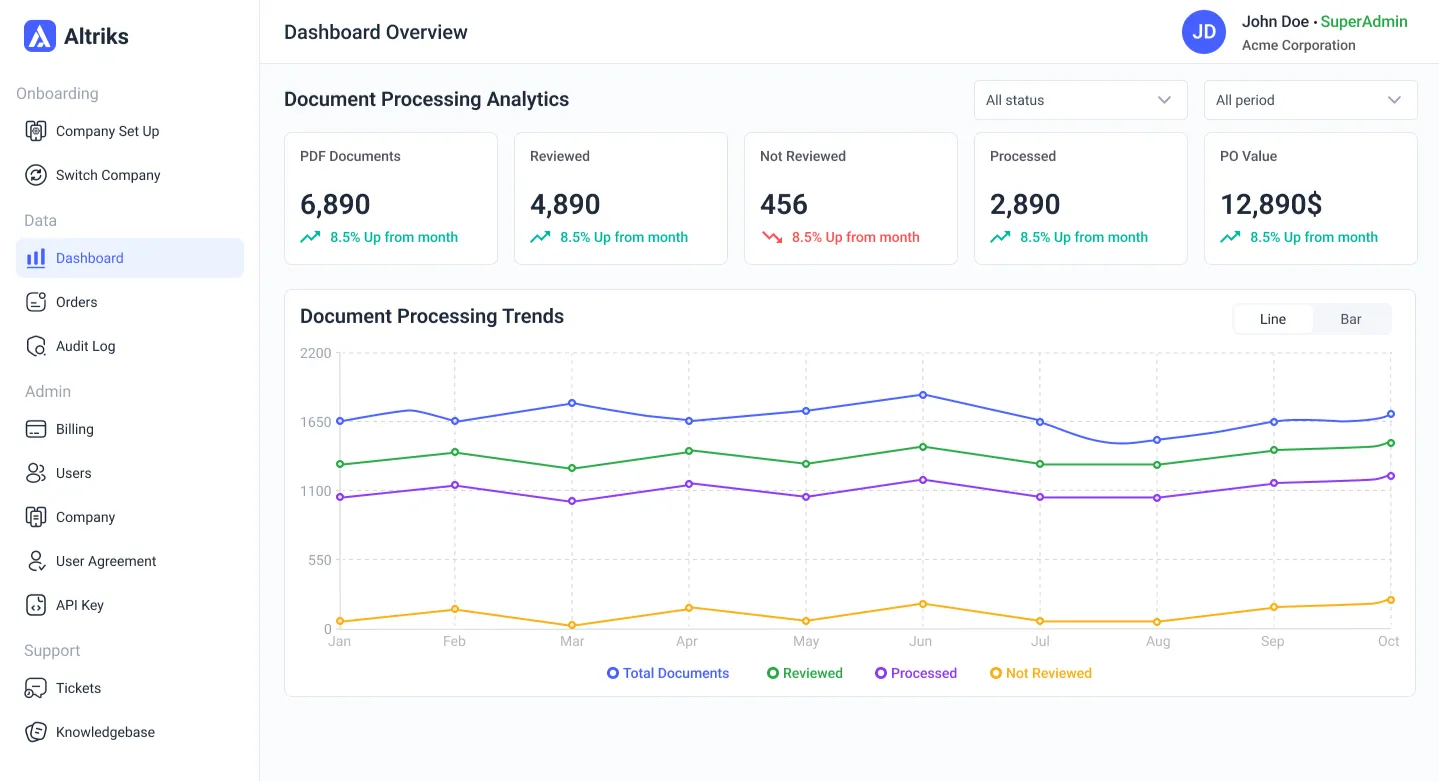
Our AI ingests EDI (X12/EDIFACT) and PDF/email attachment, detects partners and auto-routes-each document.
No Templates to maintain
Accurate data extraction
Line items, Quantities. ship to Po numbers, pricing and data and captured and validate against your master data.
Automated Posting
Real time API sync to your ERP with audit logs, notifications and dashboards for througout, SLA's and Exceptions.
Key Features
In-Depth Explanation of Our Automation Features
Your Partner in Turning EDI/PDF order into clean,
ERP-ready data-fast accurate & fully auditable.
Uses AI to read unstrctered order data in PDF
Extract key elements like order header, line items price, Qty, ship to, bill to etc, and display item in human readable form for your customer service reprensetives for further verification.
Evaluates EDI (X12/EDIFACT) documents and auto process the EDI orders
Our standard EDI conversion program can convert compile EDI (X12) 850 docs into human redable standard JSON fromat and transmit them to your ERP system.
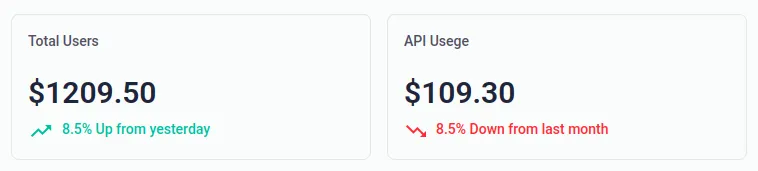
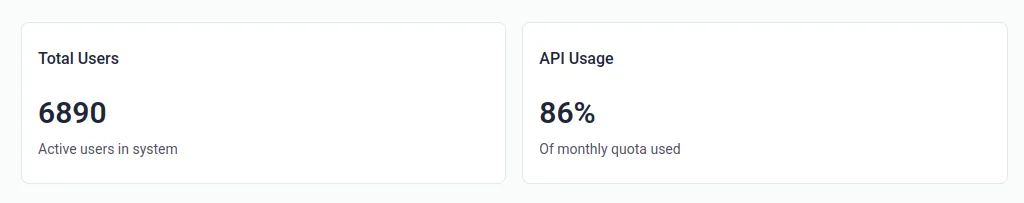
Our Dashboard will show you both EDI and PDF order data metrics
Your CSR can monitor and support orders from all your customers in one dashboad, You can also reprocess the failed orders from one control system
Learn More Details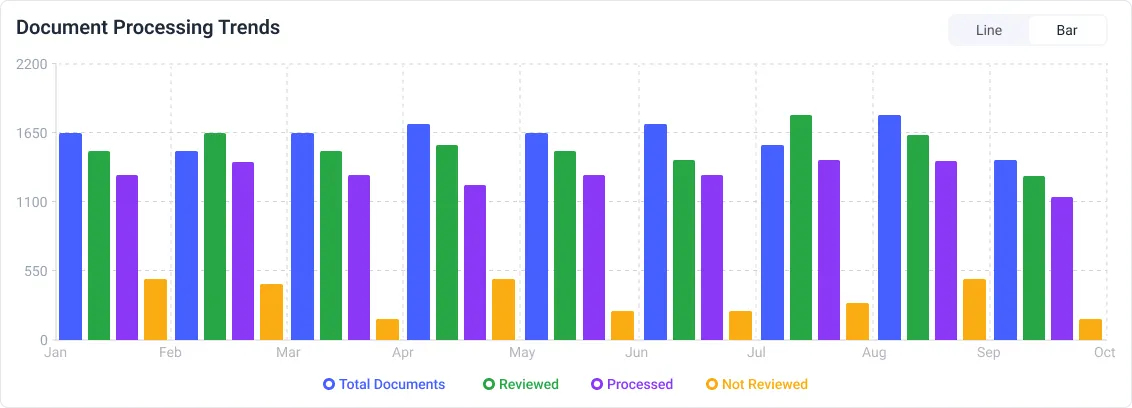
Pricing & Plan
Choose a suitable plan
Your Trusted Partner in Structured & Un-Structured data
processing.
Basic Plan
Ideal for small businesses or individuals looking to secure their data with fundamental protection features.
- Dashboard Access
- No customer limit
- Daily Data Backup
- Email Support
- Single User License
Premium Plan
RecommendedPerfect for medium to large businesses requiring security features and priority support.
- Dashboard Access
- No customer limit
- Daily Data Backup
- Email Support
- 24/7 Priority Support
- Multi-User Licenses (Up to 50 Users)
12,000+ Happy Customers
Customer Reviews
Your Trusted Partner in Data Protection with Cutting-Edge Solutions for
Comprehensive Data Security.
Implementing this data security solution has been a game-changer for our company.
The real-time threat detection and automated response features have significantly reduced our risk exposure. We now feel more confident than ever about our data security posture.

IT Director at HealthCare
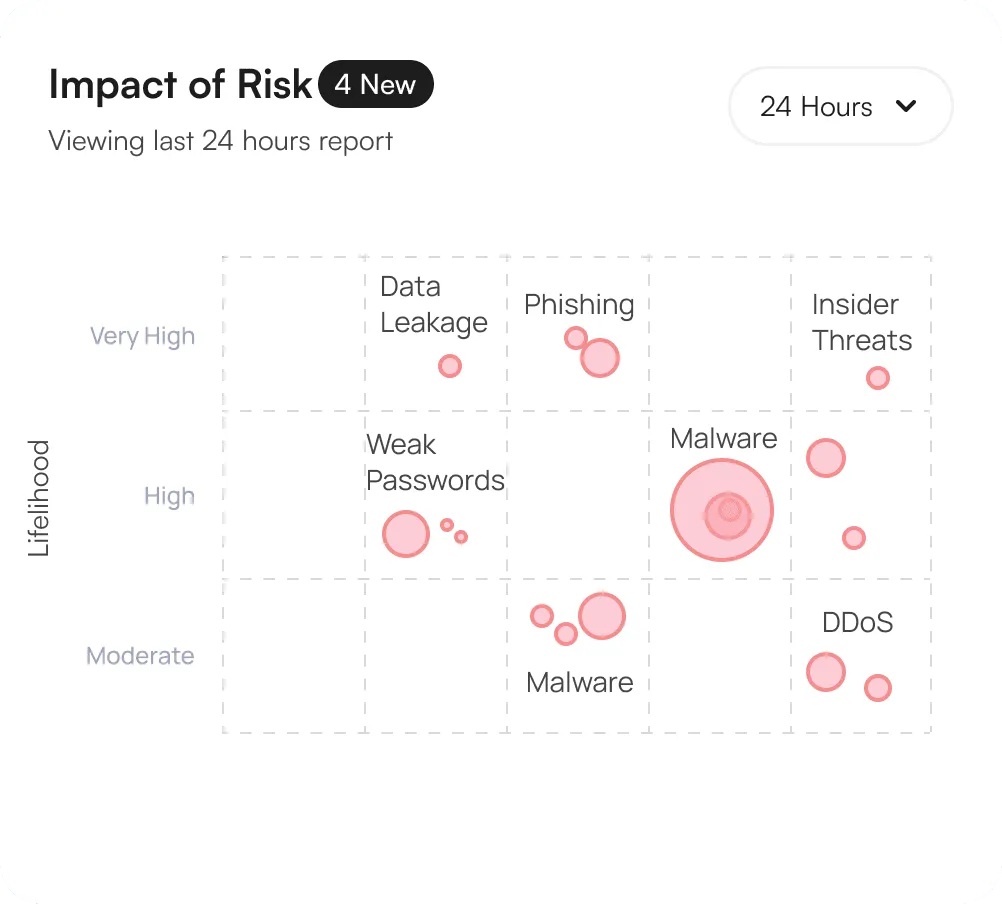
The granular access controls and detailed user activity tracking have given us unparalleled visibility.
The granular access controls and detailed user activity tracking have given us unparalleled visibility into our system's security. This platform has helped us maintain our data.

CTO at Tech Innovators Inc.
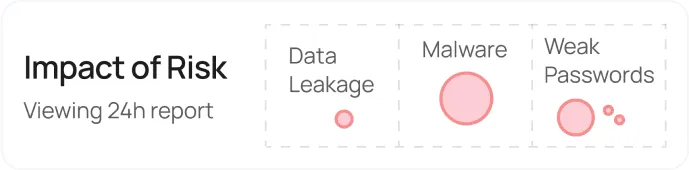
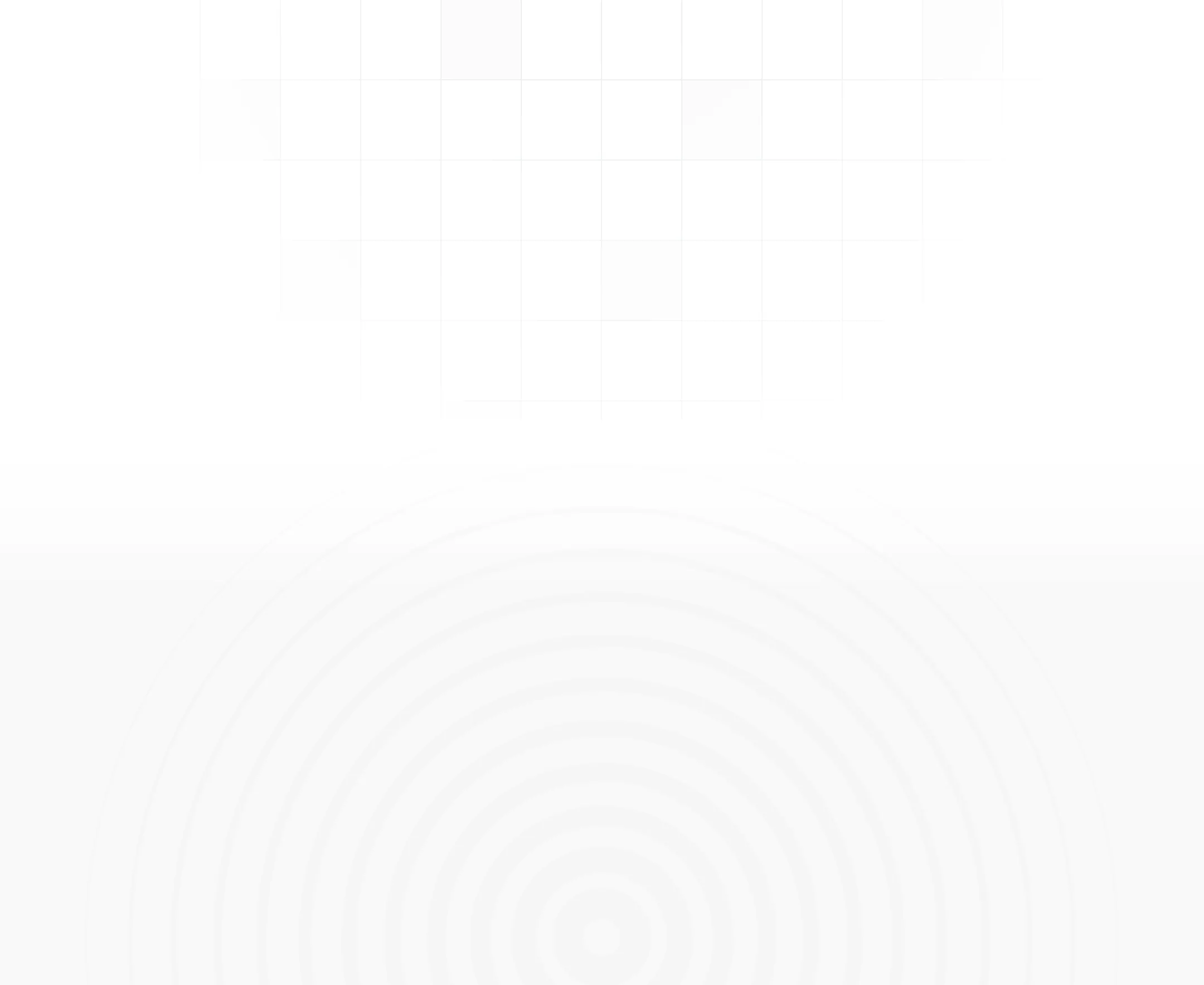
The comprehensive risk analysis and impact visualization tools are exceptional.
The comprehensive risk analysis and impact visualization tools are exceptional. We can quickly identify and mitigate potential threats before they become serious issues.

COO at Financial Services Group
Secure Your Data with Altriks Protection Solution
Allows you to set thresholds for security parameters and receive real-time alerts when these thresholds are breached.
Get Started